There are many tools and methods to conduct cyber threat hunting in a Microsoft 365 environment, but sometimes you just need a way to get some useful data that you can analyze quickly to answer that age old question “have we been hacked?”.
In my opinion, Microsoft doesn’t make it easy to answer this question (at least not without making you buy some extras). So as a follow-up to a previous post, I decided to write a simple script to help you answer the question yourself.
Don’t expect any bells or whistles, this script is meant to be a proof-of-concept related to my previous statement that a tool “doesn’t have to be pretty it just has to be pretty useful“.
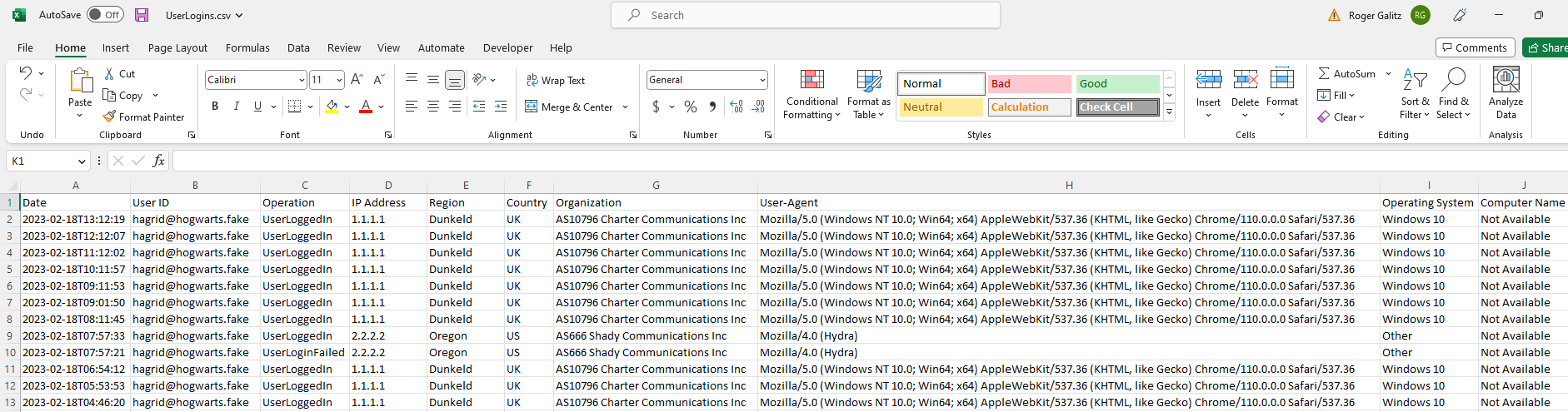
One of the most useful features of this tool is that it collects up to the last 50,000 records of login data (success and failure).
Microsoft only allows you to collect 5,000 at a time unless you follow a somewhat convoluted process…this script does all the convoluting so you don’t have to.
It also looks up information about the source IP addresses and extracts some of the most important data out of Microsoft’s AuditData property so you can actually use it.
All you have to do is execute the script, and you should end up with a handful of files in the current directory that have all the info you need to get started hunting.
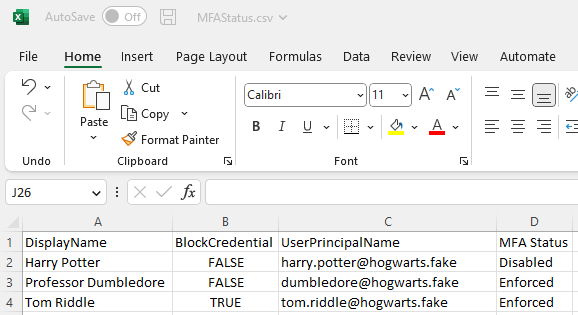
Here are some examples of the type of data the script collects:
User login data (successful and failed logins)
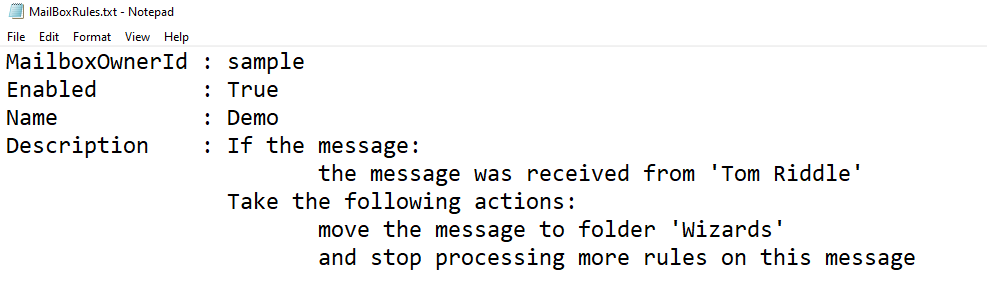
Mailbox rules
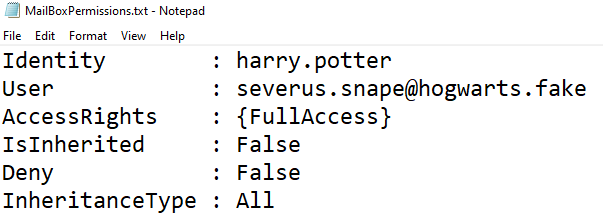
Mailbox permissions
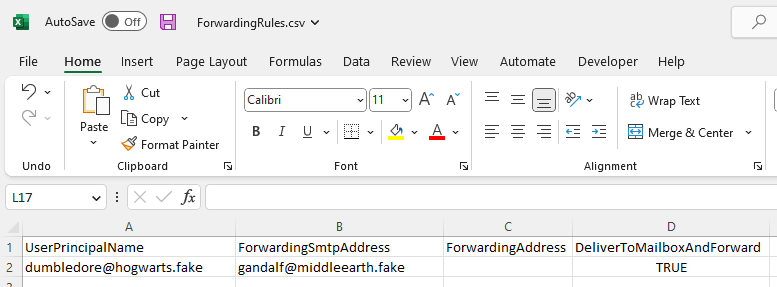
Forwarding Rules
MFA Status
The script can be downloaded here: https://github.com/5shield/m365cth
That’s it for now, good luck, and happy hunting!
